There is two common way to check TLS certificate revocation status:
- Certificate Revocation List (CRL)
- Online Certificate Status Protocol (OCSP)
The second option is more faster and modern way to do that. The OCSP link must be presented some way to do that. There are at least two options:
- Your Certificate Authority (CA) automatically puts that OCSP link into your certificate
- You go to the guys in your CA and asks them for the OCSP link.
There is how you can check if your SSL certificate contains OCSP link:
- Your cert must contain Authority Information Access (AIA) extension
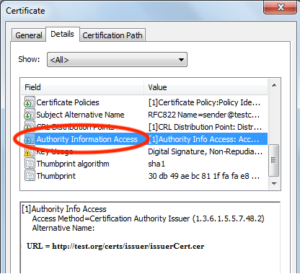
- If you don’t see OCSP link in first point, you must scroll down information into this section to the second point
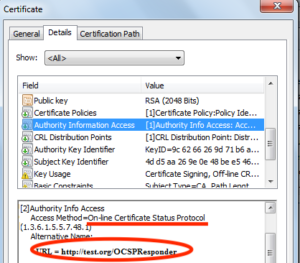
If you certificate contains OCSP link
- Add
-Dcom.sun.net.ssl.checkRevocation=trueflag when you run your jar - Set
Securityproperty from inside your code:java.security.Security.setProperty("ocsp.enable", "true")
After you perform this, every time Java sees new TLS connection, it is going to OCSP CA server through the link from AIA section of TLS certificate, check the revocation status, and reject the connection if certificate was revoked.
If your certificate does not contain OCSP link
- Add
-Dcom.sun.net.ssl.checkRevocation=trueflag when you run your jar - Set
Securityproperty from inside your code:java.security.Security.setProperty("ocsp.enable", "true") - Go to the guys from your CA and asks them for OCSP link
- Set one more
Securityproperty inside your code:Security.setProperty("ocsp.responderURL", url)
P.S.: there might be one case, when OCSP server itself has specific SSL cert. If so, you need to set other Security properties manually:
Security.setProperty("ocsp.responderCertSubjectName", certSubjectName)
Security.setProperty("ocsp.responderCertIssuerName", certIssuerName)
Security.setProperty("ocsp.responderCertSerialNumber", certSerialNumber)
Technical details
If you interested in how this works under the JVM hood, you might want to see this classes:
java.security.cert.PKIXRevocationChecker, class declaration is: public abstract class PKIXRevocationChecker extends PKIXCertPathChecker
sun.security.provider.certpath.RevocationChecker, class declaration is: class RevocationChecker extends PKIXRevocationChecker
You can navigate into sun.security.provider.certpath.RevocationChecker class just by pasting this line into IntelliJ IDEA and clicking on the class name with CTL+left click ignoring error (red glow).
You can see, how RevocationChecker class reads Security properties in method:
private static RevocationProperties getRevocationProperties() {
....
rp.ocspEnabled = ocspEnabled != null
&& ocspEnabled.equalsIgnoreCase("true");
rp.ocspUrl = Security.getProperty("ocsp.responderURL");
rp.ocspSubject
= Security.getProperty("ocsp.responderCertSubjectName");
rp.ocspIssuer
= Security.getProperty("ocsp.responderCertIssuerName");
rp.ocspSerial
= Security.getProperty("ocsp.responderCertSerialNumber");
rp.crlDPEnabled
= Boolean.getBoolean("com.sun.security.enableCRLDP");
}Useful links
http://www.pkiglobe.org/auth_info_access.html
https://docs.oracle.com/javase/6/docs/technotes/guides/security/certpath/CertPathProgGuide.html#AppC
https://stackoverflow.com/questions/40823206/how-to-enable-ocsp-in-x509trustmanager
https://tersesystems.com/blog/2014/03/22/fixing-certificate-revocation/
If you still have any questions, feel free to ask me in the comments under this article or write me at promark33@gmail.com.
If I saved your day, you can support me 🤝